Open-source vulnerabilities continue appearing frequently. It is increasingly difficult to patch them all before cybercriminals take advantage of them and exploit them. While there are efforts in place at the industry and government level to strengthen the security of open-source projects, development companies using open-source components need a faster solution.
Open-source vulnerabilities continue appearing frequently. It is increasingly difficult to patch them all before cybercriminals take advantage of them and exploit them. While there are efforts in place at the industry and government level to strengthen the security of open-source projects, development companies using open-source components need a faster solution.
Implementing software composition analysis (SCA) can provide the early detection and fix needed to stay ahead of attacks. This post will explain why SCA can be a critical tool you should use.
The challenges of open-source vulnerabilities
Open-source software offers several advantages. These projects can be used for free and commercial projects and are typically continuously improved by a community of collaborators. They also tend to be transparent, so developers can see the code and modify it. No wonder most software projects contain open-source code then.
Still, open-source software presents challenges and security risks. Every now and then, we hear about a critical vulnerability found in an open-source component, library, or application, which puts companies at risk.
One example could be the detection in December 2021 of a critical vulnerability in a popular Java logging library (Log4j). As companies rushed to patch the issues, attackers were already exploiting the vulnerabilities—three more were discovered in the meantime—with ransomware. Then, without time to rest, in late January 2022, Linux distributions got threatened by a local privilege escalation (LPE) vulnerability in PolKit, the component for setting security and access policy.
Why is open-source software so prone to vulnerabilities? Open-source projects are delivered for free with no real accountable party in the case of a security flaw. The transparency of an open-source project can present a risk, too. When a vulnerability is discovered, the community learns quickly about this, which means attackers can also find out and act on it.
Why do we need to end the detection, disclosure, patching cycle?
As open source components and projects become more popular, it is crucial to increase their security and find a way to eliminate vulnerabilities early on in the process. The current cycle of detection, disclosure and rush to patch needs to end, as it turns into a sort of whack-a-mole game between security teams and attackers. Focusing on fixing vulnerabilities as soon as possible is the goal of many industries and public agencies. Focusing on fixing vulnerabilities as soon as possible is the goal of many industries and public agencies.
The widespread adoption of open-source projects compounds the problem. Even if you find vulnerabilities, the dependency tree is so complex that you cannot close the project.
The Open Source Security Foundation (OpenSSF) announced in February 2022 a project to strengthen the security of 10,000 of the most popular deployed projects. This project consists of two sections, Alpha and Omega.
The Alpha section will target and evaluate the most critical open-source projects. The goal of this stage is to discover and address security gaps. Yet, the task of selecting and prioritizing which open-source projects should receive help is not an easy one. Included in the list are large open-source projects, such as the Postgres database. But as more vulnerabilities appear the list changes. The Omega stage will act after the list of the 10,000 open-source projects is closed. It will combine a team of experts with technology and processes to identify and fix critical vulnerabilities.
All these efforts are worthwhile, of course, but what can you do as a company to prevent, discover and fix vulnerabilities in your open-source components? Here is where software composition analysis can help.
How Software composition analysis identifies open-source risks
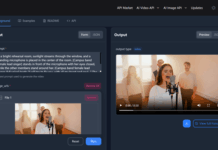
 Software composition analysis (SCA) is an application security analysis tool that identifies what open-source components and dependencies you have in your application and how they are used. This tool helps you evaluate potential risks coming from open-source components and strengthens the security of your software development process.
Software composition analysis (SCA) is an application security analysis tool that identifies what open-source components and dependencies you have in your application and how they are used. This tool helps you evaluate potential risks coming from open-source components and strengthens the security of your software development process.
As most application developers use reused code, the risk of borrowing a code with bugs or vulnerabilities increases. You can also face a problem with conflicting licenses. Security teams cannot review the components of a hundred libraries manually. Moreover, most probably, these libraries have other dependencies, which have more dependencies.
SCA tools scan the open-source components and dependencies and generate a software bill of materials (SBOM). The SBOM will include the component’s name, release date, license information, and version number.
Tips for working securely with open-source
With all risks involved, you may wonder how to work securely with open-source software? Thankfully, there are several tips you can implement to improve the security of your projects:
- Use software composition analysis: These tools can give you a comprehensive understanding of what open-source components you have and the risks entailed. Some SCA tools can scan your application’s manifest and generate a list of dependencies. Others scan the artifacts, using binary fingerprinting to identify open-source components. The most powerful software composition analysis tools will use a hybrid approach and scan both manifests and binaries.
- Analyze the risks and find how to compensate for them: Once you have the open-source components mapped, analyze the risks involved and define how you will fix them.
- Before adding open-source components, analyze the project: It is even more critical to implement best practices like analyzing an open-source component before adding it to your project. Look for curated software where the components were previously tested.
- Stay updated for patches and warnings: keeping an eye for news of warnings, patches, and updates, can help you respond early to threats.
Summary
The fight against open-source vulnerabilities is far from over. Combining industry efforts with a robust internal security posture can help companies face these threats. Among them, using tools such as software composition analysis can give you a step ahead to early detection.